Security and reliability
Security isn't just a feature—it's a cornerstone of trust and reliability. From edge to cloud, and every point in between, we embed security into the very fabric of our products and services. With a relentless commitment to staying ahead of emerging threats, we deliver robust defenses that safeguard your data, applications, and infrastructure.

CISA Secure by Design pledge
HPE is committed to providing our customers with the most secure products possible. In May 2024, HPE voluntarily signed the Cybersecurity and Infrastructure Security Agency’s Secure by Design pledge. You can read more about our progress in meeting this pledge here.
Security at every layer
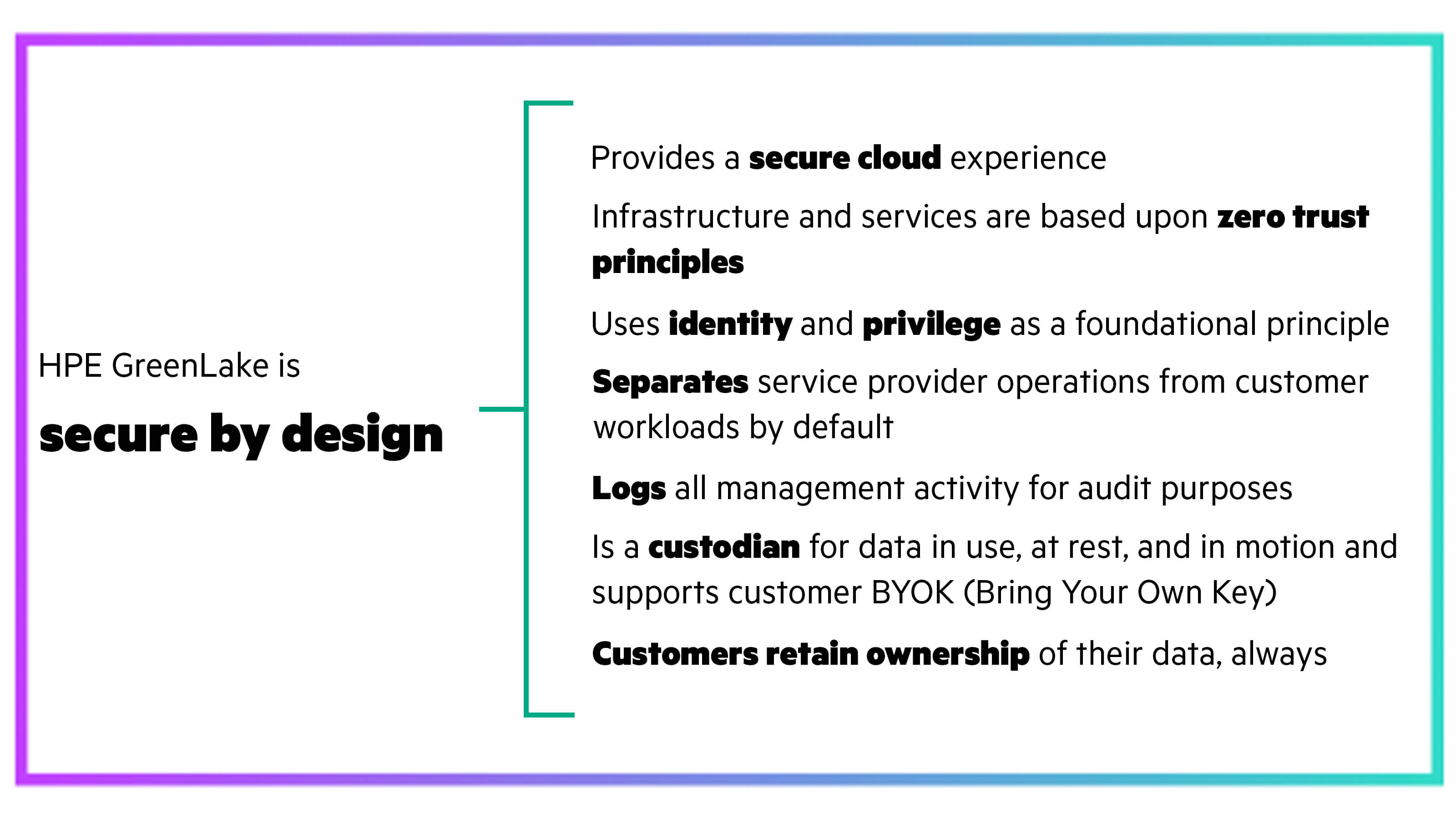
Our approach to secure by design begins even before the first byte of code has been written or the first chip has been soldered. At HPE, we believe that we have a responsibility to our customers to ensure that every product and every service that we deliver is built using secure by design principles.

Product security overview
At Hewlett Packard Enterprise (HPE), product security isn’t just a priority—it’s a core part of our DNA. Our Product Security Office (PSO) is the central catalyst and partner entrusted with ensuring the high standards of security across our product portfolio.
By embedding security into every stage of our product development, we not only protect our innovations but also reinforce HPE’s belief in product security as a key component to provide our customers with the trust and confidence to use our products.
Integration of security into development
HPE integrates security into every stage of product development through its SDL, following NIST Secure Software Development Framework (SSDF) guidelines and using advanced automation tools to ensure robust security measures.
Response to product vulnerabilities
At HPE, the Product Security Response Team (PSRT) stands as the frontline defense in responding to and mitigating security vulnerabilities across all our products. Our dedicated team meticulously triages, tracks, escalates, and resolves every report of vulnerability, supporting and maintaining high standards of security and compliance.
Comprehensive management of security reports
PSRT is committed to driving reported security vulnerabilities to completion. We negotiate coordinated responsible disclosures with development teams and researchers, to address issues promptly and effectively. Our team publishes detailed security bulletins to the HPE Support Center, documenting issue resolutions and tracking compliance with internal security policies.
Collaborative efforts with industry leaders
We receive vulnerability reports from a diverse range of sources, including internal development teams, customers, security researchers, and renowned security research organizations. These collaborations are crucial for coordinating public responses and ensuring the security of products that integrate their technologies.
Authority in vulnerability management
As the designated CVE Numbering Authority (CNA) for HPE, PSRT registers, scores, and issues CVE numbers for vulnerabilities in all our products. This authority underscores our commitment to transparency and accountability in vulnerability management.
Transparency in vulnerability reporting (CVEs)
The official list of HPE Security Bulletins covers all CVEs that impact products affecting HPE customers, including software and firmware from other suppliers included in our products. For software and firmware implemented by HPE, we provide both CWE and CPE and undertake to make the information in CVEs accurate.
Reporting potential vulnerabilities
The Hewlett Packard Enterprise (HPE) Product Security Response Team (PSRT) is responsible for receiving, tracking, managing, and disclosing vulnerabilities in HPE products. The HPE PSRT actively works with industry, non-profit, government organizations, and the security community when vulnerabilities are reported. A security vulnerability is defined as any weakness in a product that allows an attacker to compromise the confidentiality, integrity, or availability of a product, customer infrastructure, or IT system through an HPE product in that environment.

Continuous cyber defense
Our Cyber Defense Center serves as our global cybersecurity operations headquarters and houses our incident response analysts. 3.5 billion events are recorded by our SIEM every day. The team analyzes data to detect, investigate, and respond to potential cyber threats by monitoring around the clock operating from state-of-the-art facilities in Galway, Ireland, Houston, Texas, and Bangalore, India. In addition, HPE has implemented formal incident response processes which align to incident notification regulations.
The GreenLake unified platform experience continuously applies more than 2,000 separate security controls to protect customers and their data in real time.

Ponemon Institute: The 2025 Global Study on closing the IT security gap: Addressing cybersecurity gaps from edge to cloud
The lack of visibility and control over users and devices in your edge-to-cloud environments is widening the IT security gap. The 2025 Ponemon Institute study lists out security strategies that high-performing teams use to minimize hidden threats within their IT infrastructure.

Zero trust security: A new approach to security architecture
Cybercrimes cost the world trillions of dollars every year. Defend your business against relentless attacks with robust security solutions.